Megaupload.com, one of the world's most popular sources of online piracy, has been shut down by a federal indictment issued Thursday, which seized and charged seven people connected with it with running an international enterprise based on internet piracy. Online piracy by the two companies - Megaupload Ltd and Vestor Ltd - generated more than $ 175 million in criminal proceeds and caused more than half a billion dollars in harm to copyright owners
Hacking group Anonymous said Thursday it knocked out the websites of the FBI, U.S. Department of Justice, and several entertainment industry sites as retribution for anti-piracy efforts by both the government and the entertainment industry. Anonymous said it was "the largest attack ever," with 5,635 participants involved in bringing down the sites. The two government sites were up and running again after several hours.
Megaupload stood as one of the most popular file storage services on the internet, allowing users to upload and share files that included movies and music, among other media. With a timeliness that borders on satirical, public uproars over antipiracy bills SOPA and PIPA in Congress ran in tandem with the arrests and seizure.
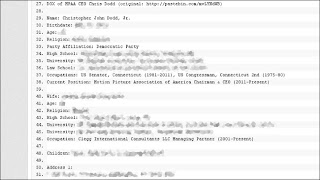 Anonymous have compiled and published a dossier containing personal information about employees of the Motion Picture Association of America (MPAA) and US Democratic party leaders and their families.
Anonymous have compiled and published a dossier containing personal information about employees of the Motion Picture Association of America (MPAA) and US Democratic party leaders and their families.
 Anonymous have compiled and published a dossier containing personal information about employees of the Motion Picture Association of America (MPAA) and US Democratic party leaders and their families.
Anonymous have compiled and published a dossier containing personal information about employees of the Motion Picture Association of America (MPAA) and US Democratic party leaders and their families.
Megaupload has preemptively defended these charges with the following assertion:
Mega has over 150 million registered users and over 50 million daily unique visitors. Employees of over 70% of the world’s Fortune 500 companies have accounts with us. We have become the de-facto standard for sending files that are too big to email. We are the most popular hard disk in the cloud. We host more backups than any other company. If Mega is a rogue operator as we have been unfairly labelled by the MPAA and RIAA, then what about Google? What about Yahoo? And every single ISP? At any given time, they all host pirated, illegal or even criminal content for which they are not liable nor legally obliged to prevent their users from posting. They are, like Megaupload, online service providers who are in no position to monitor or restrict their users’ activities. There are technical, practical and legal reasons why these entities as a whole enjoy safe harbor protection all over the world. Service providers like Megaupload are simply better off focusing on providing a better service to their customers than fending off lawsuits from third parties unhappy about content.
That said, all service providers have to deal with the challenge of online piracy, just like us. Google probably hosts the world’s largest index of pirated content and yet no one has characterized them as rogue. Why not sue the manufacturers of external USB hard drives or burnable DVDs? They can be used for illegal purposes, too. Microsoft’s Windows operating system is the world’s largest enabler of piracy. Windows is used to transfer and consume pirated content on a massive scale every day. And yet Microsoft is not rogue. This double standard should not be imposed on Megaupload since it finds no basis in either logic or the law. All we want is equal treatment.